
We Secure
Your Things
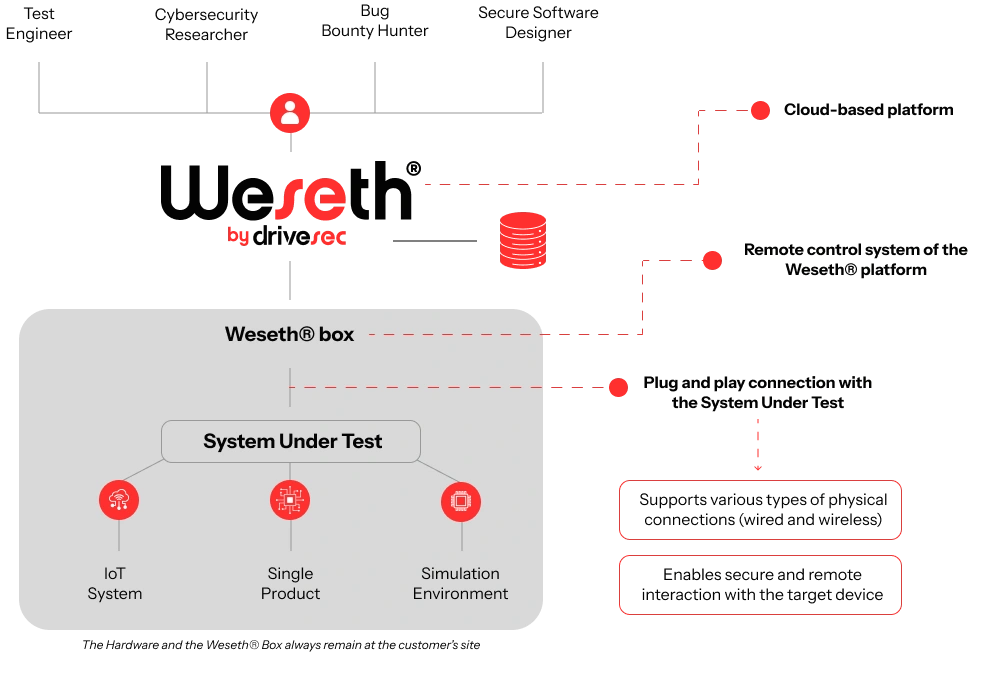
Weseth® is an ecosystem of security solutions designed to revolutionize the approach to security testing and validation through automation and secure remote access.
Weseth® reduces testing time and costs, empowering companies to become more autonomous, security-aware, and resilient against digital threats.
How it Works




Rotate your device for a better experience
Benefits
ZERO SETUP TIME
Weseth® is easy to use and can be self-
installed within 1 hour, without impacting IT
infrastructure.
FLEXIBILITY
Weseth® can be used to connect every
type of system with any type of interface,
can be programmed and can support
remote checks (through Digital I/O
management).
SECURITY
Weseth® is fully managed and monitored
to guarantee security, integrity, and prevent
tampering.
CAPABILITIES
The features and the number of potential
use cases supported by
Weseth® overpass solutions available on
the market.
ZERO SETUP TIME
Weseth® is easy to use and can be self-
installed within 1 hour, without impacting IT
infrastructure.
FLEXIBILITY
Weseth® can be used to connect every
type of system with any type of interface,
can be programmed and can support
remote checks (through Digital I/O
management).
SECURITY
Weseth® is fully managed and monitored
to guarantee security, integrity, and prevent
tampering.
CAPABILITIES
The features and the number of potential
use cases supported by
Weseth® overpass solutions available on
the market.
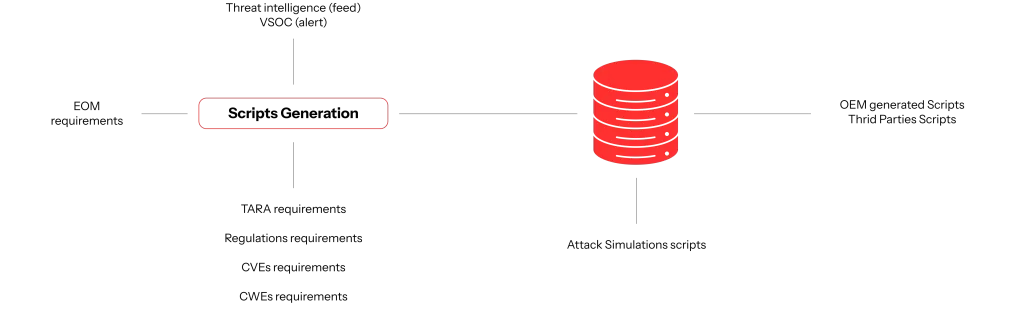
The Knowledge Base
The Knowledge Base initially contains a set of scripts designed by Drivesec for the customer, which can be automatically executed via Weseth® to simulate cyberattacks, test resistance to fuzzing, and verify compliance with security requirements.
This database is a dynamic asset: the number of scripts it contains continuously grows thanks to new inputs, allowing the Knowledge Base to remain constantly updated and tailored to the customer’s needs.
This database is a dynamic asset: the number of scripts it contains continuously grows thanks to new inputs, allowing the Knowledge Base to remain constantly updated and tailored to the customer’s needs.
Thanks to this approach, project after project, the customer becomes increasingly autonomous in cybersecurity testing, avoids repeating previously encountered design mistakes, and enhances their ability to identify vulnerabilities before the product goes into production.


Rotate your device for a better experience
Use Cases
Weseth® supports the automated and remote execution of test cases for verifying the security of the device.
Specifically, the integrated scripts continuously assess the effectiveness of security countermeasures, compliance with certification requirements, and resilience against fuzzing and common attacks.
Specifically, the integrated scripts continuously assess the effectiveness of security countermeasures, compliance with certification requirements, and resilience against fuzzing and common attacks.
Thanks to an intuitive and user-friendly Graphical User Interface (GUI), even users without specific cybersecurity expertise can easily use Weseth®, optimizing operation.


Rotate your device for a better experience
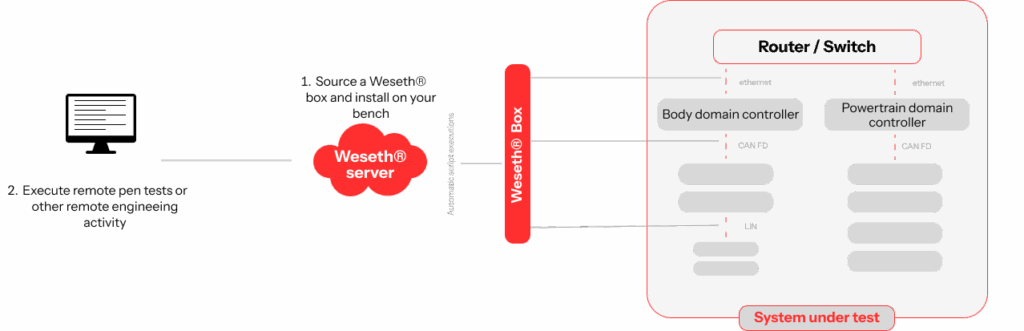
Weseth® supports the execution of penetration tests, including those conducted as part of
bug bounty programs, which team members can perform remotely, securely, and directly
on the IoT device connected to the Weseth® Box.
Since this use case requires advanced cybersecurity expertise, Drivesec can provide
support on request through its specialized internal team.

Rotate your device for a better experience
Weseth® is designed as a high-engineering solution, fully adaptable and customizable to support a wide range of use cases, including data collection, device control, system monitoring, software patching, cooperative vulnerability fixing, and more, all performed remotely and securely.
Contact us to find out how
Weseth® can meet your specific needs.
Supported Standards and Regulations
China
Chinese Cybersecurity Regulation (eg. GB 44495)
Chinese Cybersecurity Regulation (eg. GB 44495)
UNECE/WP29 – harmonization of vehicle Regulation
General Safety Regulation includes Cybersecurity and SW Update
(UN Regulation No. 155 and 156)
General Safety Regulation includes Cybersecurity and SW Update
(UN Regulation No. 155 and 156)
European Union
Cyber resilience Act
RED II
Cyber resilience Act
RED II
United States NHTSA
Cybersecurity Guidelines Vehicle Communication – Requirement Self Drive Act
Cybersecurity Guidelines Vehicle Communication – Requirement Self Drive Act
European Union
Cyber resilience Act
Cyber resilience Act
European Union
Cyber resilience Act
Machine Regulation
European Union
Cyber resilience Act
RED II
Machine Regulation
ISO 18031
European Union
Cyber resilience Act
RED II
Cyber resilience Act
RED II
China
Chinese Cybersecurity Regulation (eg. GB 44495)
Chinese Cybersecurity Regulation (eg. GB 44495)
UNECE/WP29 – harmonization of vehicle Regulation
General Safety Regulation includes Cybersecurity and SW Update
(UN Regulation No. 155 and 156)
General Safety Regulation includes Cybersecurity and SW Update
(UN Regulation No. 155 and 156)
United States NHTSA
Cybersecurity Guidelines Vehicle Communication – Requirement Self Drive Act
Cybersecurity Guidelines Vehicle Communication – Requirement Self Drive Act
European Union
Cyber resilience Act
Cyber resilience Act
European Union
Cyber resilience Act
Machine Directive
Cyber resilience Act
Machine Directive
European Union
Cyber resilience Act
RED II
Machine Directive
Cyber resilience Act
RED II
Machine Directive

